Vulnhub Empire LupinOne

Vulnhub Training Waklthrough – Empire LupinOne
Knowledge
- ffuf – find secret file
- base58 encode
- dirty_pipe privilege eslacation
- linpeas – a script that search for possible paths to escalate privileges on Linux/Unix*/MacOS hosts
- Python Library Hijacking
- Privilege Eslacation with pip
1. Environment Setup
Download the zip file, extract it and import into VMware or VirtualBox.
2. Reconnaisence
1. IP Address
arp-scan to scan the ip addr:
|
|
2. Port Info
nmap scan:
|
|
Enable port info:
| port | service |
|---|---|
| 22 | ssh |
| 80 | http web |
nmap result display a robots.txt file, access:
|
|
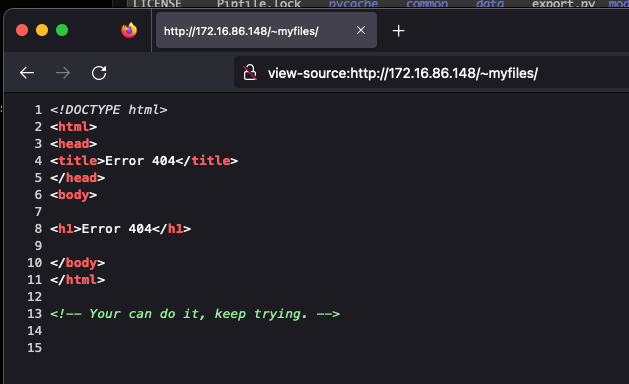
And can not access ~myfiles, but it give us a hint sting, keep a mind in it.
3. Web Directory
Let us scan the web directory:
|
|
Nothing useful.
3. Exploit
1. Look for ssh private key
Ok, return the ~myfiles, let’s fuzz the path of it:
|
|
Well done, we found a secret file:
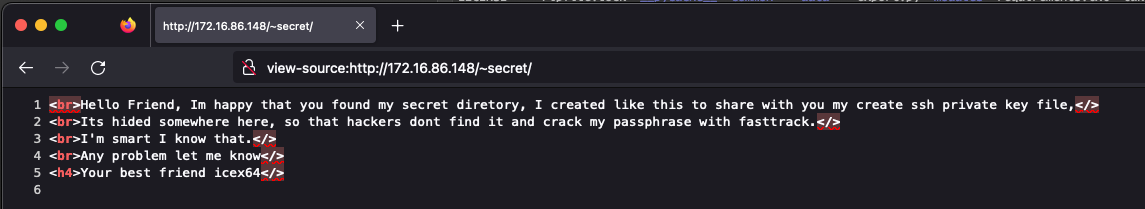
Fine, we need to find out the ssh private key file. As we all know, the ssh private key named .[key_file], so we should fuzz ~secret/.[file]:
|
|
Let’s access the file:
|
|
2. unpasswd the ssh private key
Well, the key file has passphase, we need to unlock it.
It’s like has been encoded, check it:
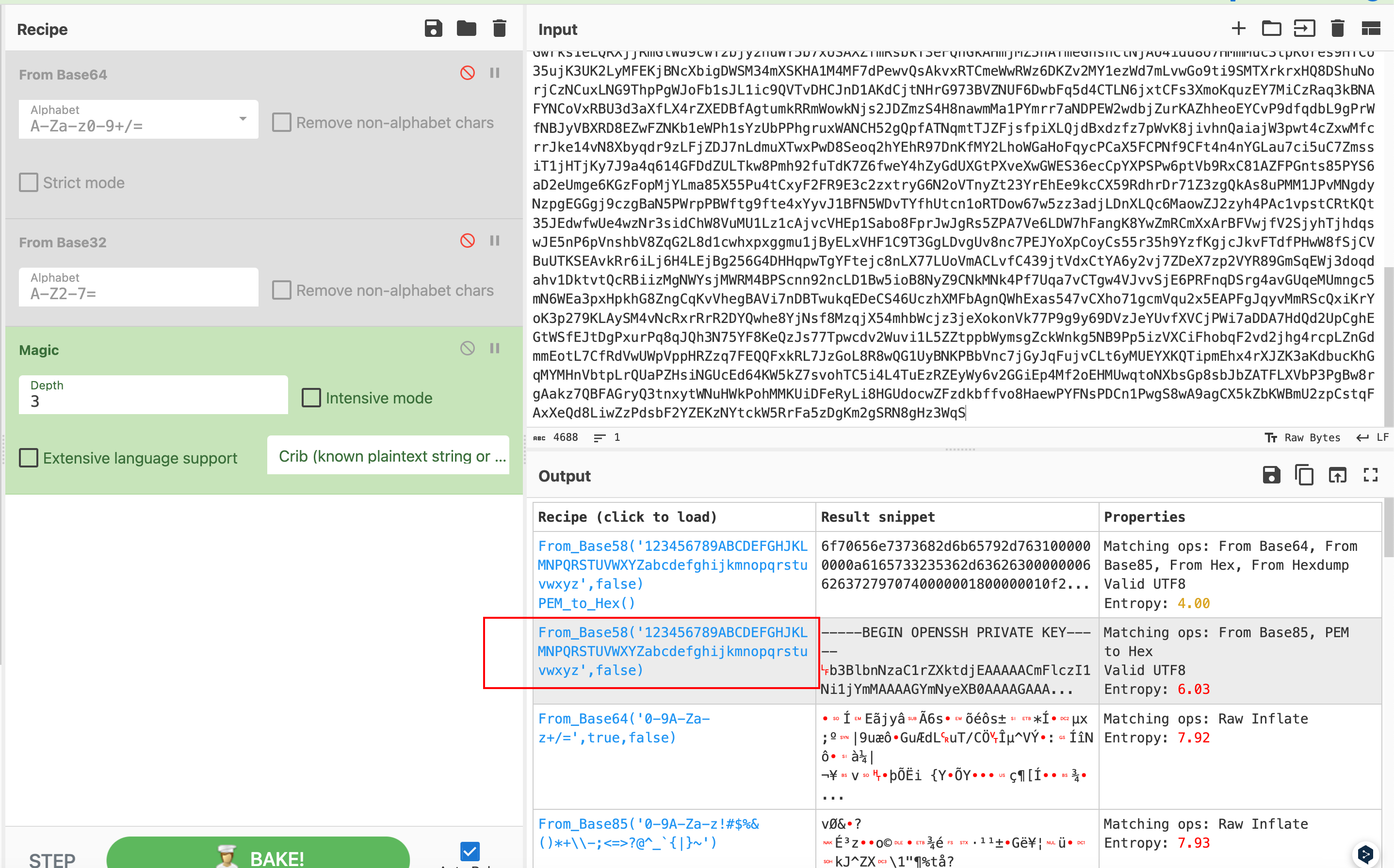
It is encoded by base58, so decode it:
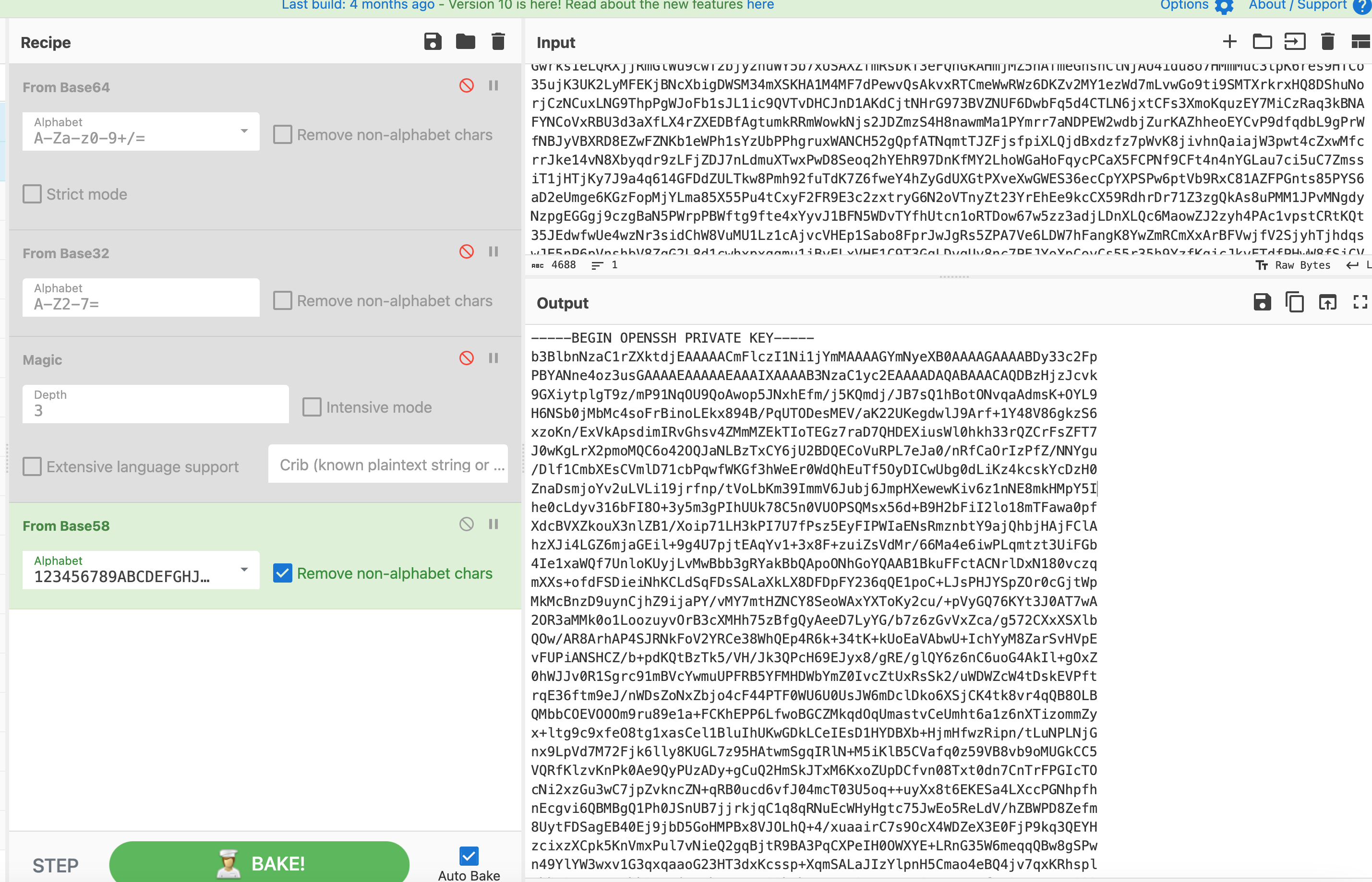
We got the private key file. And then broute force it with john:
|
|
Now, we can login ssh with user icex64 and private key:
|
|
4. Privilege Escalation
Now, we need to get root privilege.
1. First method - Dirty_PIPE
We found that the target has gcc, and kenel version is 5.10.0, so we can use dirty_pipe vulnerability to get root:
|
|
Thsi way is easy, but maybe cause the kernel crash, or root can not login.
2. Second method - LinPEAS
Download and execute LinPEAS.sh:
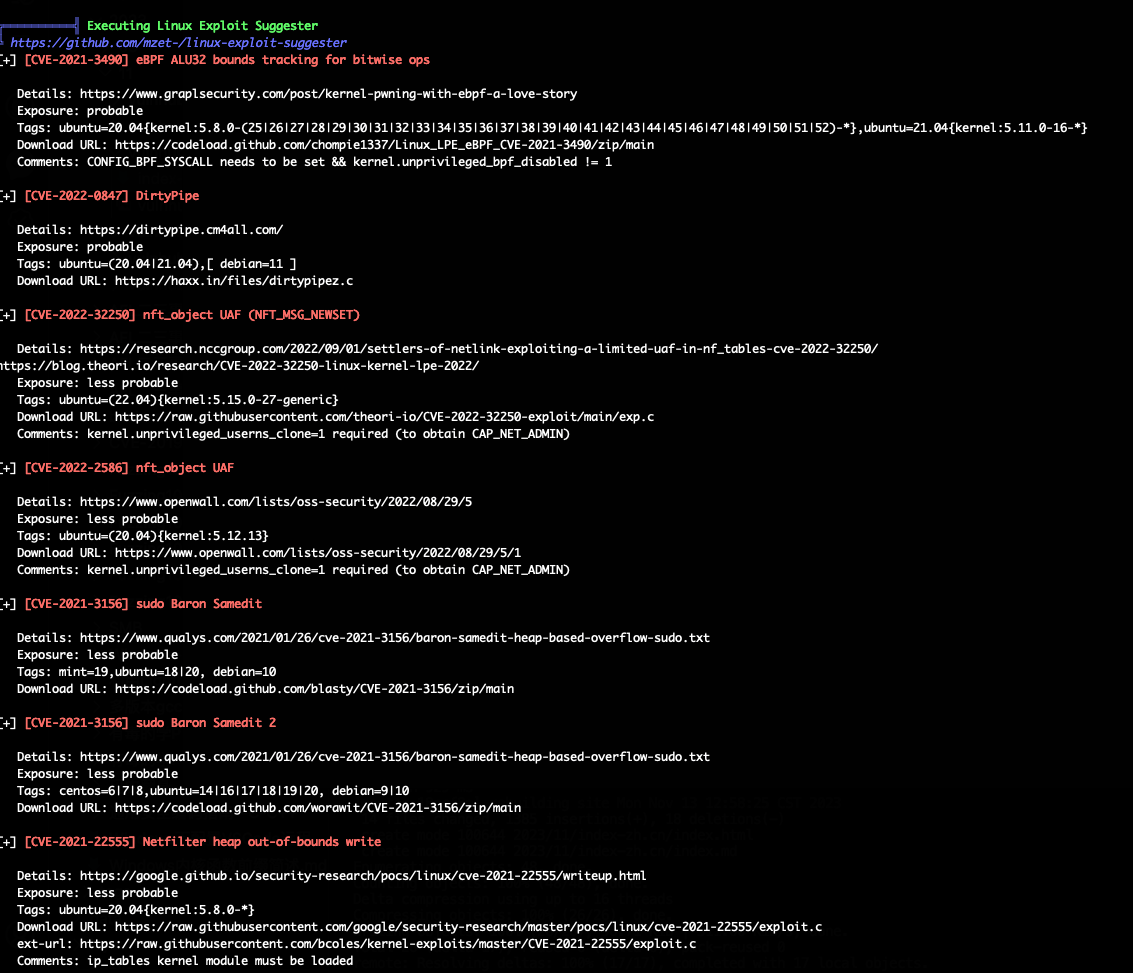
And we can see some exploit suggester:
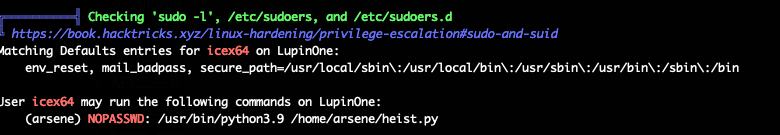
And we can see user icex64’s privilege info:
And we found some writable files:
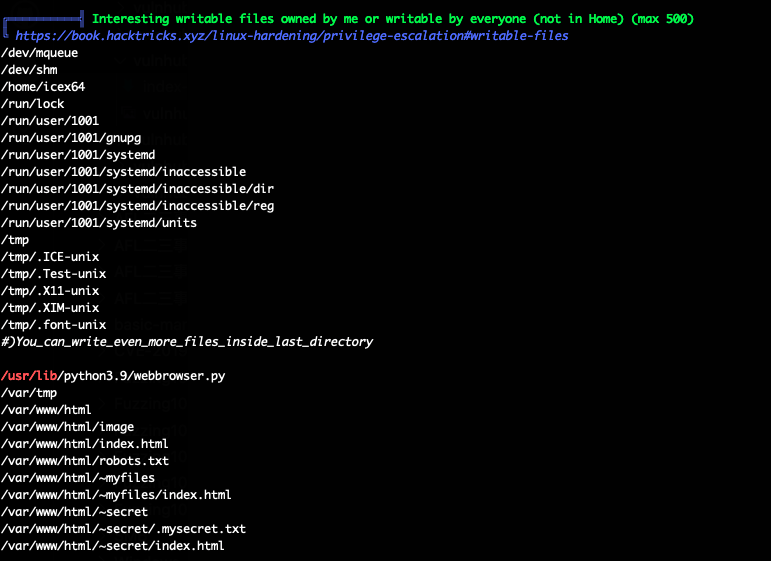
As we know, the file /home/arsene/heist.py content like follow:
|
|
and the file webbrowser.py is writable. So, we can change the /usr/lib/python3.9/webbrowser.py file to achive the root.
Modify the file /usr/lib/python3.9/webbrowser.py as follows, add some payload:
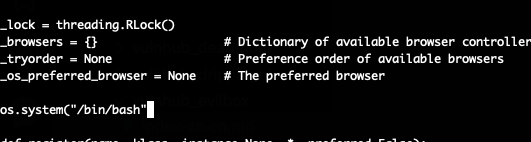
And then execute the heist.py file:
|
|
Well, how we can get root? Condiser the sudo -l:
|
|
The pip application has root privilege, so we can use it:
|
|
 V4ler1an
V4ler1an